Implementing ISO 27001:2013
ISO 27001 is the only auditable international standard which defines the requirements for an information security management system (ISMS). This standard covers all types of organisations and information formats, and is not simply an IT related ISO standard. All information used by organisations of any size, is covered by the standard, this includes electronic and hard copy formats as well as information that is known by employees and suppliers.
The standard is designed to ensure the selection and implementation of adequate and proportionate information security controls . ISO 27001 helps to protect information assets and give confidence to interested parties including an organisation’s customers. The standard adopts a process approach for establishing, implementing, operating, monitoring, reviewing, maintaining, and continually improving an organisation’s ISMS. The standard preserves the confidentiality, integrity and availability of information by applying a risk management process and gives confidence to interested parties that risks are managed effectively and appropriately. These three core attributes are defined as follows:
- Confidentiality – ensuring that information is accessible to only those authorised to have access
- Integrity – safeguarding the accuracy and completeness of information and processing methods
- Availability – ensuring that authorised users have access to information and associated outputs when required
The intent is that this standard should be integrated with other management systems such as quality (ISO 9000 series), environment (ISO 14001), health and safety (OHSAS 18001) and business continuity management (ISO 22301).
The standard itself is constructed around Schewart's original Plan, Do, Check, Act cycle of continuous improvement, often called Deming's cycle. The 10 specific clauses are highlighted in the diagram below:
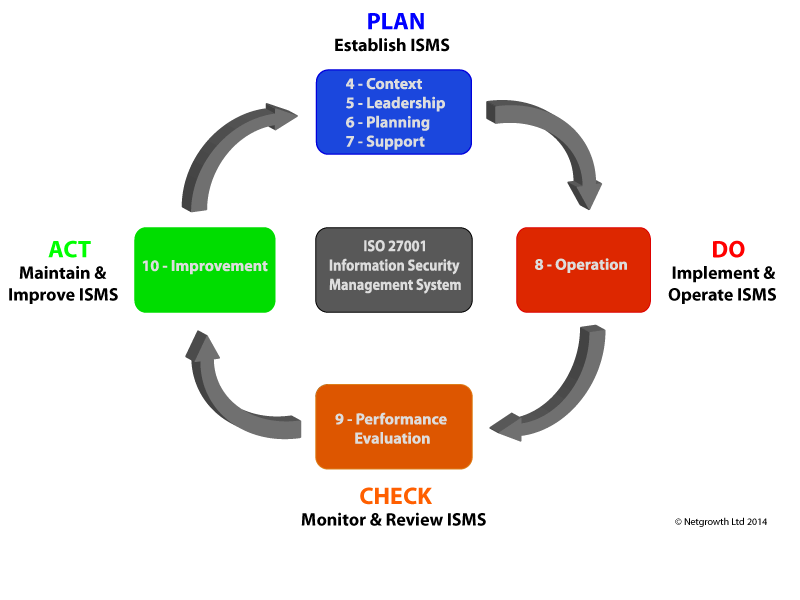
The development of an ISMS represents a proactive, systematic and logical approach to address the challenges of information security, rather than a piecemeal approach to security breaches. Organisations are faced with increasing information security risks, be they internal or external, the standard enables effective risk management to counter these organisational threats.
Deciding to implement an ISMS is a significant challenge to the organisation, even if an accredited quality management system exists, it will involve a great deal of work throughout the organisation. The ISMS cannot become the preserve of one person, as the system is pervasive and must be effectively operated throughout all defined activities within the organisation. This standard requires total commitment and participation from the leadership of the organisation. The implementation process can be broken down into a six step process as illustrated below:
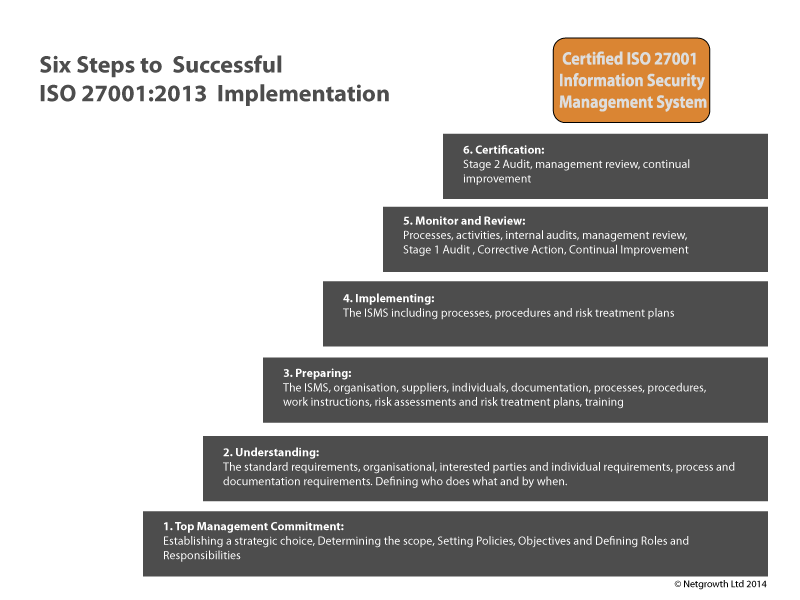
NetGrowth can help you to develop and implement your ISMS in accordance with the requirements of the ISO/IEC 27001:2013 standard. For more information please contact sales@netgrowthltd.co.uk